Root certificates are at the very core of Public Key Infrastructure (PKI), and they’re signed by trusted Certificate Authorities, or CAs. Browsers, applications, and other programs have a pre-packaged root store that signifies that these certificates are trustworthy. If you visit a website that supports HTTPS but isn’t using a certificate signed by a CA in your browser’s root store, then the website will be flagged as not secure. Typically, applications and browsers can update their certificates, but your phone can’t unless it’s via an OTA update. That may change with Android 14, according to Esper.
There have been a couple of scares over the years relating to certificates, and that’s because of our reliance on them as the core of a chain of trust when we visit websites. Here on XDA, our certificate is signed by Let’s Encrypt, a non-profit CA. Their certificate is signed by the Internet Security Research Group, and it’s that chain of trust that ensures that your connection to this website is safe and secure. The same goes for any other website that you visit that uses HTTPS.
Every operating system has its own built-in root store, and Android is no different. You can actually view this root store on your Android smartphone by navigating to security and privacy in your device’s settings. From there, it will depend on the type of device you’re using, but the screenshots below show where it is on OneUI 5.
The thing is, though, that even this root store isn’t the end-all and be-all. Apps can elect to use and trust their own root store (which Firefox does), and they can accept only specific certificates (dubbed certificate pinning) in an effort to avoid Man-in-the-Middle (MITM) attacks. Users can install their own certificates, but app developers have needed to opt-in to allowing their apps to use these certificates ever since Android 7.
Why having updatable root certificates is important
With Let’s Encrypt certificates being cross-signed by the Internet Security Research Group, a lot of the internet is reliant on the ISRG’s security. If ISRG lost control of its private key (should it be stolen, for example), then the ISRG would have to revoke the key. Depending on how companies respond, then it may be the case that some parts of the internet would become inaccessible to devices that don’t have updatable root certificates. While that’s a completely catastrophic nightmare scenario (and purely hypothetical), it’s the exact kind of scenario that Google wants to avoid. That’s why what’s happening with TrustCor currently might be signaling to Google that it’s time to add updatable root certificates to Android.
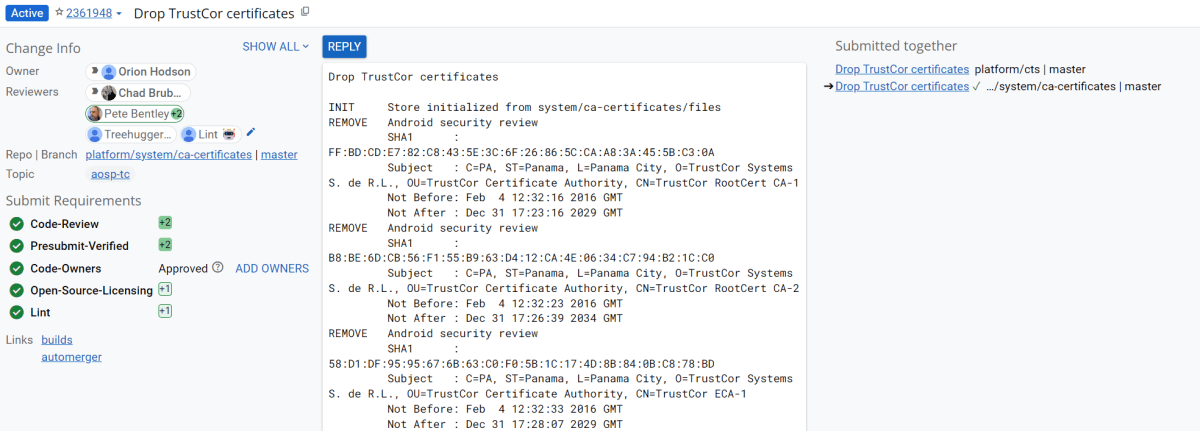
For context, TrustCor is one such certificate authority that has come under scrutiny after researchers alleged it had close ties to a US military contractor. TrustCor hasn’t lost its private key, but it has lost the trust of many companies that need to decide what certificates they include in their root stores. Those researchers alleged that the US military contractor TrustCor was close with had paid developers to place data-harvesting malware in smartphone apps. In PKI, trust is everything, and TrustCor lost that trust once those allegations came to light. Since then, companies like Google, Microsoft, and Mozilla have dropped TrustCor as a certificate authority. Removing TrustCor’s certificates from the Android root store will require an OTA update, though, and while the commit is already made in AOSP, it’ll likely be a long time until you or I actually have the update that drops TrustCor’s certificates from our devices.
The upside is that you can disable TrustCor’s certificates on your device now by going to your certificates on your device, as we showed above, and then scrolling to TrustCor and disabling the three certificates that come with your device. According to developers from the GrapheneOS project, there should be “very little impact on web compatibility due to this CA barely being used by anyone other than a specific dynamic DNS provider.”
The solution: Project Mainline
If you’re familiar with Project Mainline, then you can already see how this can help solve the problem. Google makes use of Mainline modules which are delivered through the Google Play Services framework and the Google Play Store. Each Mainline module is delivered as either an APK file, an APEX file, or an APK-in-APEX. When a Mainline module is being updated, the user sees a “Google Play System Update” (GPSU) notification on their device. Effectively, to deliver updates to critical components, Google has bypassed the need to wait for an OEM to roll out an update, choosing to do the task itself. Bluetooth and Ultra-wideband are two essential Mainline modules handled by Google.
According to commits on the AOSP Gerrit (spotted by Esper), Conscrypt, a Mainline module that provides Android’s TLS implementation, will support updatable root certificates in a future update. This would mean that certificates could be removed (or even added) via a Google Play System Update through Project Mainline, ensuring a much faster process should another situation like TrustCor (or worse) occur in the future. It’s not clear when this will roll out, but it’s likely that it will come to Android 14. It’s technically possible that Google may want to push it with Android 13 QPR2, but it would only benefit Google Pixel users until Android 14 reaches everyone else anyway next year. This is because other OEMs typically don’t roll out QPR updates.
The entire reason for this to exist would be so that Google can maintain control over another crucial aspect of device security without needing to rely on OEMs pushing updates instead. An OTA is currently required to update certificates, but in an emergency situation, every day where users don’t have an update could matter. Utilizing Project Mainline to ensure that users can get crucial certificate updates in time if they’re ever needed is certainly a welcome change.
Source: Esper